Why
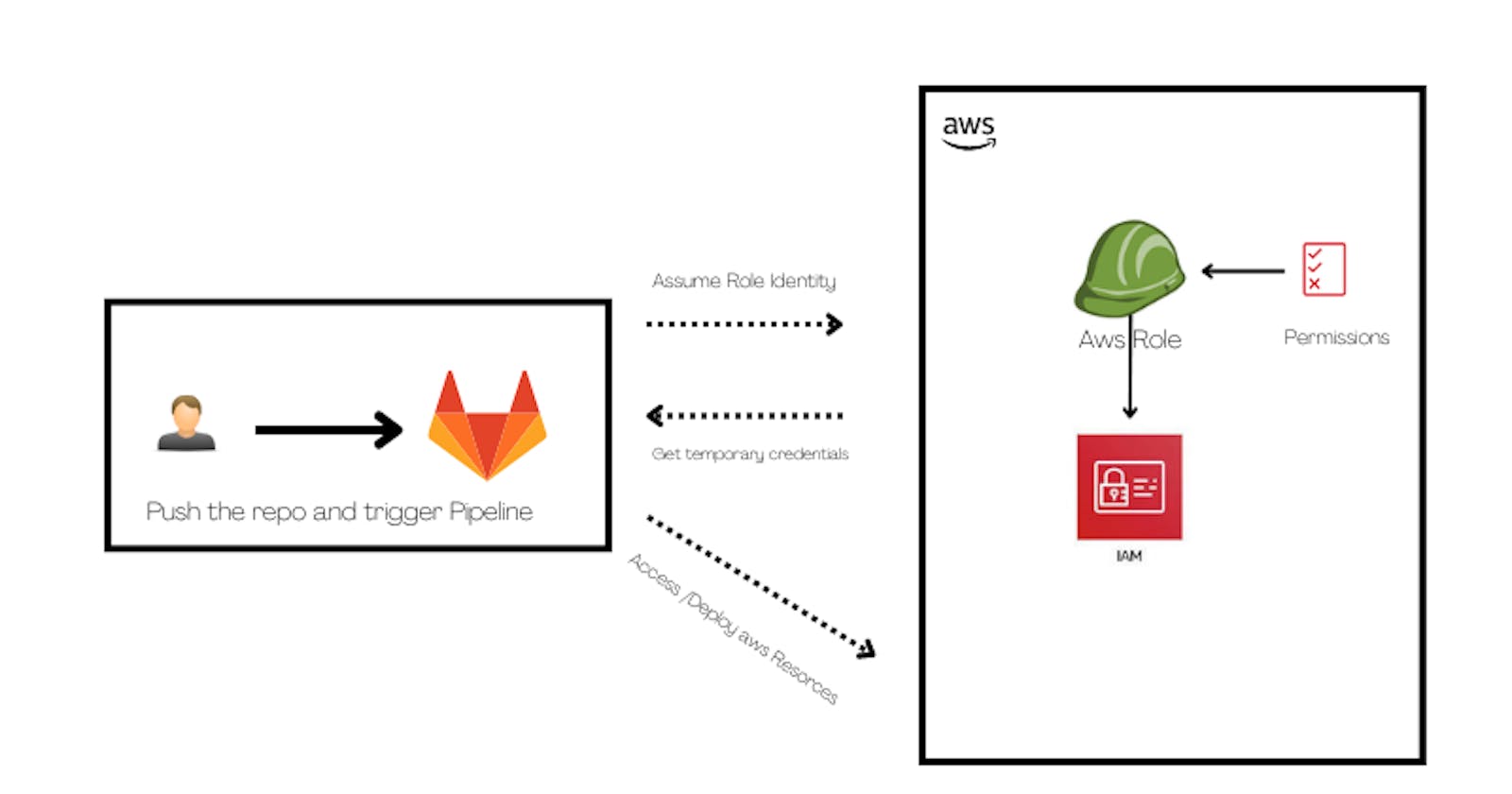
When erecting CI/ CD Channels to automate the process of planting coffers in AWS via Code( IaC- structure as Code) you need to give your channel runner authorization to emplace those coffers.
The standard way to do so is to produce credentials, which are also e.g. saved in your GitLab repo variables. These keys need to be rotated by you after around 90 days for your operation to stay secure. This might be fine if you only have one depository, but in real-life situations, you utmost of the time might be facing a situation with way more repos. You would need to take track of when to rotate the keys for each collectively if you’re working with keys.
Seems like a lot of effects to keep in mind and to take care of- and with that numerous ways to at some point- make a mistake.
How to Setup
Open the IAM console and click on identity providers,
then,
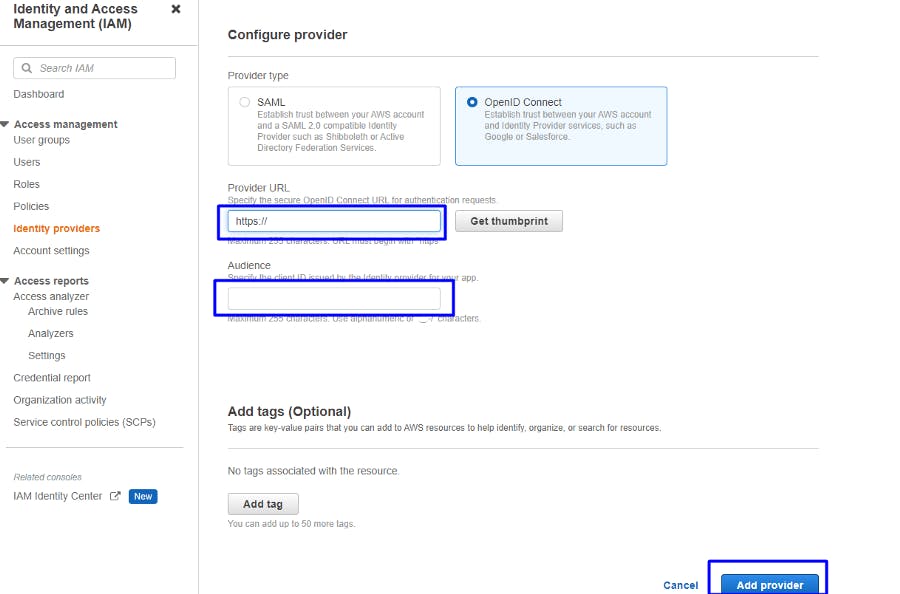
add the provider URL (https://gitlab.com) and then click on get thumbprint. and the provider audience URL same as the provider URL finally click on add provider.
Create Role and Permission
We need to assume our role that our GitLab pipeline using it and access AWS resources or use terraform script to create infrastructure.
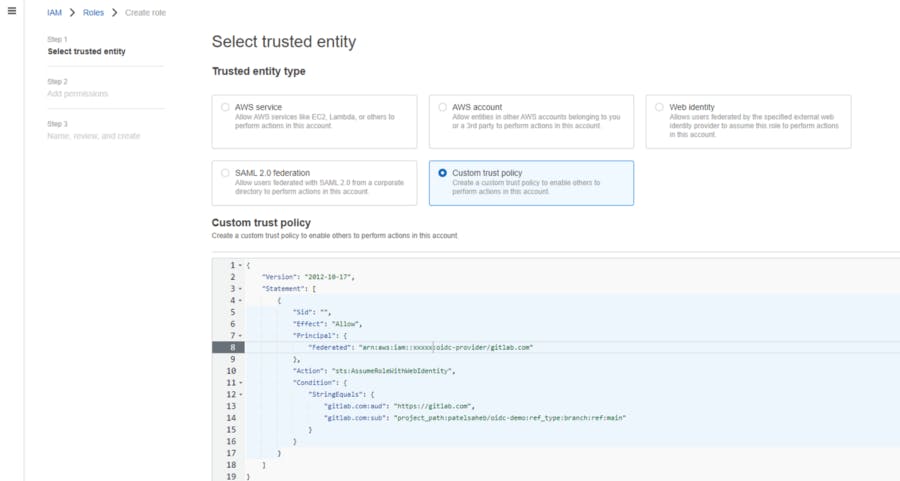
add this policy and create a role with a trusted identity. we will use this ROLE ARN in our GitLab pipeline demo.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "",
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::xxxxx:oidc-provider/gitlab.com"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"gitlab.com:aud": "https://gitlab.com",
"gitlab.com:sub": "project_path:patelsaheb/oidc-demo:ref_type:branch:ref:main"
}
}
}
]
}
Gitlab Pipeline
We need to first configure the ROLE ARN variable in GitLab project setting -> CICD,
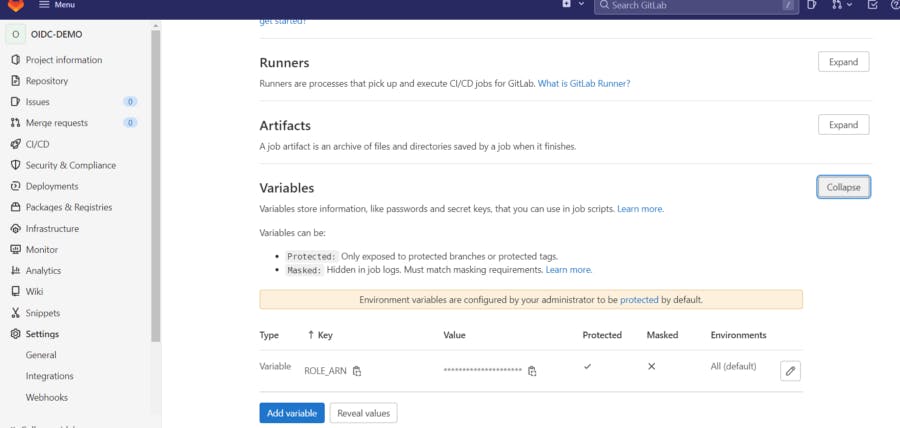
then create .gitlab-ci. YAML and add the below code in it.
image:
name: amazon/aws-cli:latest
entrypoint:
- '/usr/bin/env'
assume role:
script:
- >
STS=($(aws sts assume-role-with-web-identity
--role-arn ${ROLE_ARN}
--role-session-name "GitLabRunner-${CI_PROJECT_ID}-${CI_PIPELINE_ID}"
--web-identity-token $CI_JOB_JWT_V2
--duration-seconds 3600
--query 'Credentials.[AccessKeyId,SecretAccessKey,SessionToken]'
--output text))
- export AWS_ACCESS_KEY_ID="${STS[0]}"
- export AWS_SECRET_ACCESS_KEY="${STS[1]}"
- export AWS_SESSION_TOKEN="${STS[2]}"
- export AWS_DEFAULT_REGION=ap-south-1
- aws sts get-caller-identity
- aws s3 ls
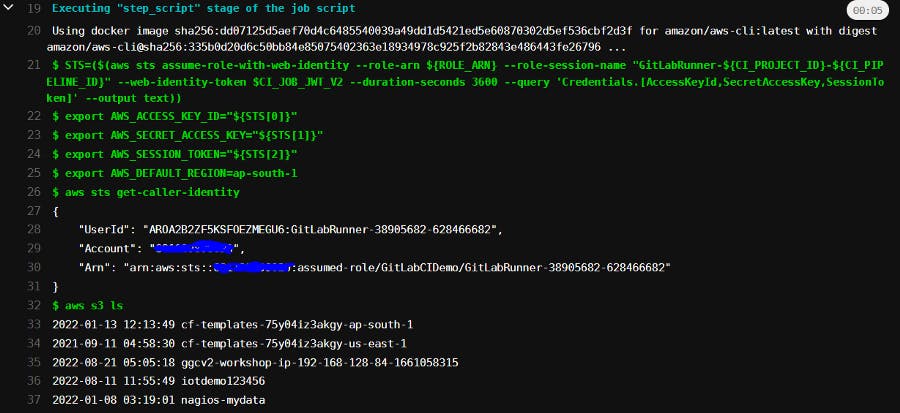
save it and run the pipeline.
you get output like the below if everything working fine.
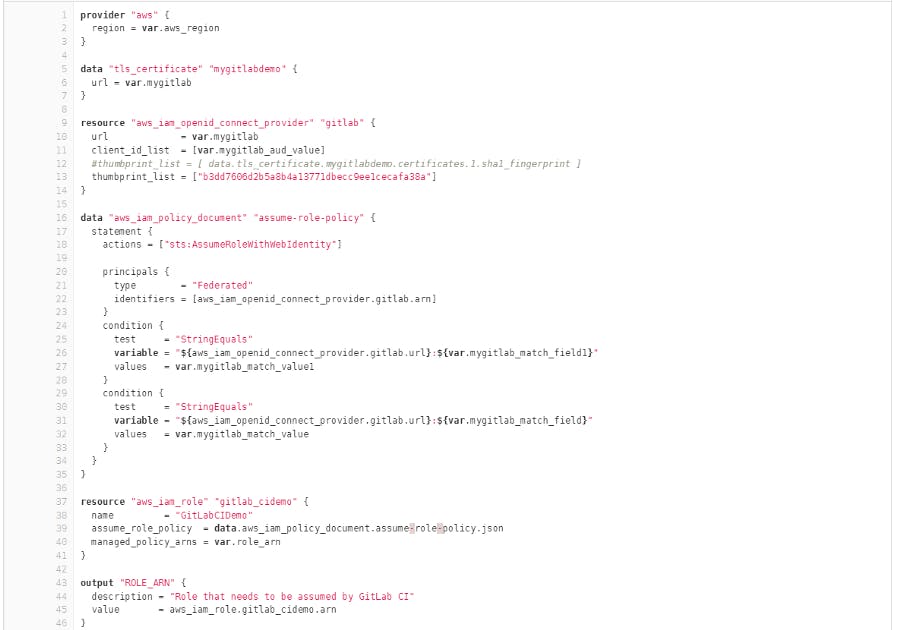
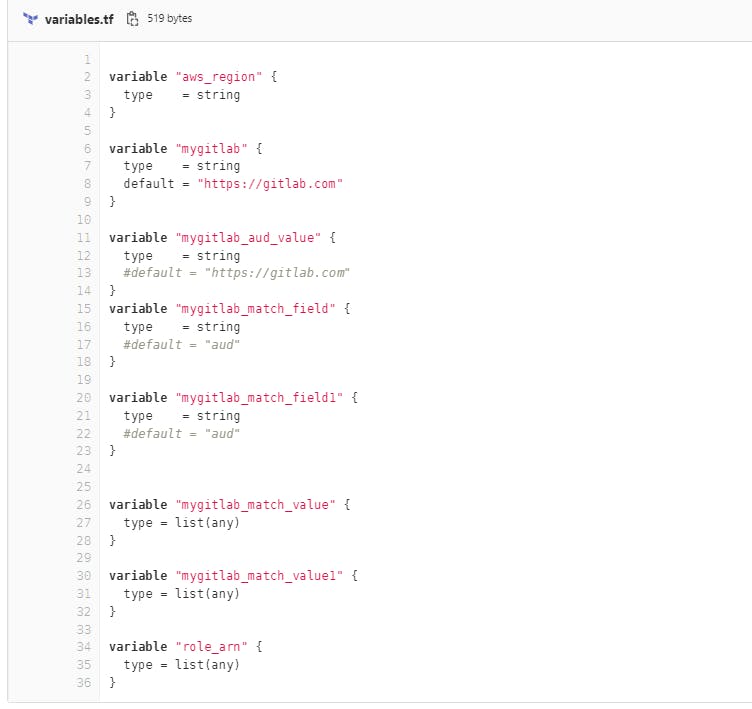
For automation of this process, I have created terraform
code as below, terraform.tfvars,
aws_region = "ap-south-1"
mygitlab = "https://gitlab.com"
mygitlab_aud_value = "https://gitlab.com"
mygitlab_match_field = "sub"
mygitlab_match_field1 = "aud"
mygitlab_match_value = ["project_path:patelsaheb/oidc-demo:ref_type:branch:ref:main"]
mygitlab_match_value1 = ["https://gitlab.com"]
role_arn = ["arn:aws:iam::aws:policy/AmazonS3FullAccess"]
main. tf code
As we see that it's easy to set up the OIDC provider and deploy your infrastructure on AWS via GitLab CI.