Table of contents
This article is about how we can configure eks cluster setup on AWS cloud. After the successful installation of eks, we will deploy the Nginx ingress controller and cert-manager and access the demo application from anywhere.
Outlines:-
Setup local environment
eks installation
deploy demo application
deploy ingress controller & cert-manager with helm3
Setup local environment (Linux-based Host machine)
setup kubectl
curl -LO https://storage.googleapis.com/kubernetes-release/release/$(curl -s https://storage.googleapis.com/kubernetes-release/release/stable.txt)/bin/linux/amd64/kubectlchmod +x ./kubectlsudo mv ./kubectl /usr/local/bin/kubectl
setup AWS CLI
pip install awscli --upgrade --user
IAM user setup
you can complete this in 2 way
- assign administrator access to IAM user
2. create a policy and attach a few AWS-managed policies to IAM users,
a. eks-policy
{
"Version": "2012–10–17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"eks:*"
],
"Resource": "*"
}
]
}
b. Cloudformation-policy
{
"Version": "2012–10–17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"cloudformation:*"
],
"Resource": "*"
}
]
}
c. AmazonEC2FullAccess
d. IAMFullAccess
e. AmazonVPCFullAccess
IAM ROLE setup
Create a new role with any name and attach the below two policies and create the role.
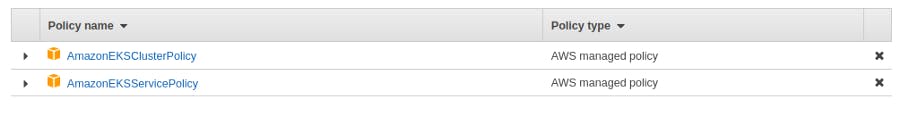
setup eksctl
curl --silent --location "https://github.com/weaveworks/eksctl/releases/latest/download/eksctl_$(uname -s)_amd64.tar.gz" | tar xz -C /tmp
sudo mv /tmp/eksctl /usr/local/bin
eksctl version
Helm 3 install
curl -fsSL -o get_helm.sh https://raw.githubusercontent.com/helm/helm/main/scripts/get-helm-3
chmod 700 get_helm.sh
./get_helm.sh
helm version
eks installation
Now, create an eks YAML file that we will use for creating eks
apiVersion: eksctl.io/v1alpha5
kind: ClusterConfig
metadata:
name: demo
region: us-east-1
nodeGroups:
- name: myNodeGroup-1
instanceType: t3.medium
amiFamily: Ubuntu2004
desiredCapacity: 3
ssh: # use existing EC2 key
publicKeyName: eksdemo
save it and hit the below command to start creating eks cluster,
save it and hit the below command to start creating eks cluster,
eksctl create cluster -f eks.yaml
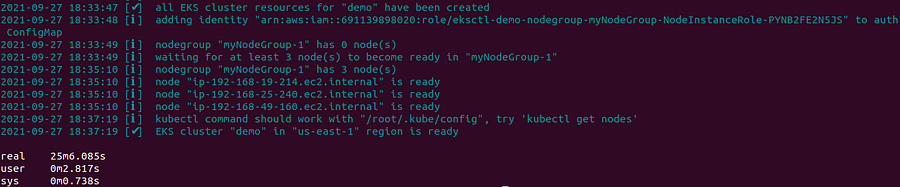
Cluster is created and now you can check nodes,
kubectl get nodes
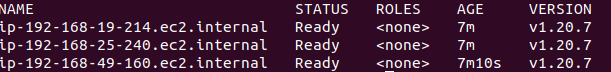
deploy demo application
we will deploy the demo nodejs application. you can get the below link,
nodejs-app-YAML
kubectl apply -f demo-nodejs.yaml
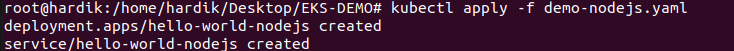
deploy ingress controller and cert-manager with helm chart.
helm repo add ingress-nginx https://kubernetes.github.io/ingress-nginx
helm install ingress-nginx ingress-nginx/ingress-nginx
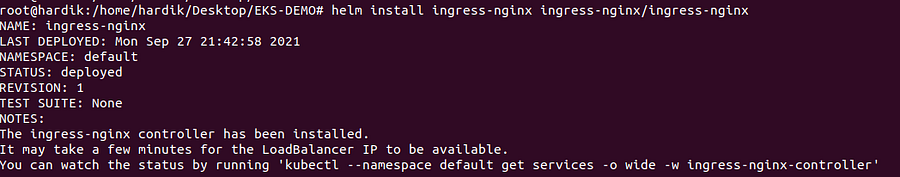
deploy cert-manager
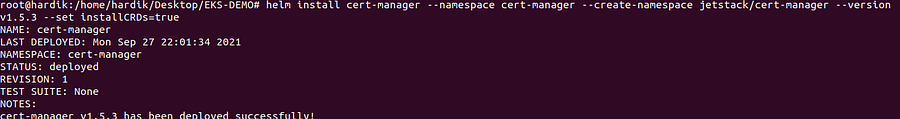
helm repo add jetstack https://charts.jetstack.io
helm install cert-manager --namespace cert-manager --create-namespace jetstack/cert-manager --version v1.5.3 --set installCRDs=true
Now create an issuer or cluster issuer and deploy
create issuer.YAML
apiVersion: cert-manager.io/v1
kind: ClusterIssuer
metadata:
name: letsencrypt-production
spec:
acme:
server: https://acme-v02.api.letsencrypt.org/directory
email: hardik.patel@domain.com
privateKeySecretRef:
name: letsencrypt-production
solvers:
- selector: {}
http01:
ingress:
class: nginx
--------
kubectl apply -f issuer.yml
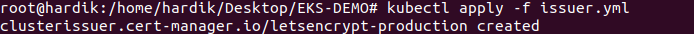
you can verify,
kubectl get clusterissuer
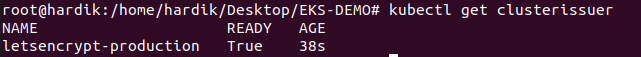
now deploy new-ingress.YAML,
kubectl apply -f new-ingress.yml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress-testing
annotations:
kubernetes.io/ingress.class: nginx
cert-manager.io/cluster-issuer: "letsencrypt-production"
#nginx.ingress.kubernetes.io/ssl-redirect: "true"
spec:
tls:
- hosts:
- node.digidatased.com
secretName: ssl
rules:
- host: node.digidatased.com
http:
paths:
- path: /
pathType: ImplementationSpecific
backend:
service:
name: hello-world-nodejs
port:
number: 80
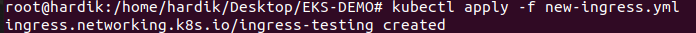
after this hit the below command, which shows us the status of SSL,
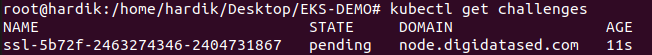
check again in a few mins you will get output like as below,
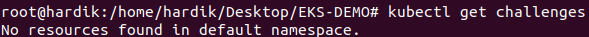
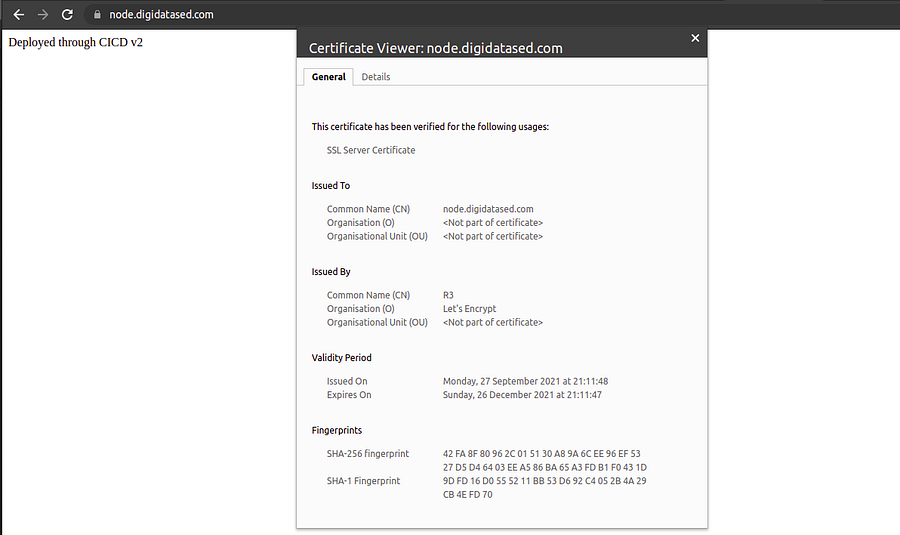
that means SSL is configured for your domain and you can hit in browser to verify,
CLEANUP
eksctl delete cluster -f eks.yaml
